Fundamentals of Ethernet
Introduction to Network Protocols
A Network Protocol is a set of rules. There are literally an ocean of protocols.
Typical common Protocols
HTTPS and HTTP
HTTPS: Hypertext transfer protocol secure – Data is encrypted before the device sends
HTTP: Hypertext transfer protocol *unsecure – Data is sent in plain text – hackers can intercept the data as its being transmitted
Transfering files
FTP: File transfer protocol – Unsecure Data is sent in plain text
SFTP: Secure file transfer protocol – Data is encrypted before it is sent
TFTP: Trivial File transfer protocol – un-encrypted other people can sniff traffic and read data
POP3: Post Office Protocol used for receiving email
IMAP: Internet Message Access Protocol used to receive messages
SMTP: Simple Mail Transfer Protocol – used for sending
HTTPS: Used to access email via Browser, traffic will be encrypted
WebDAV:
Remote device access:
Telnet: is the unencrypted version of SSH – Its unsecure, traffic / passwords can be sniffed
SSH: Very secure it uses a text based interface ( command prompt )
RDP: Remote Desktop protocol widely used my Microsoft.
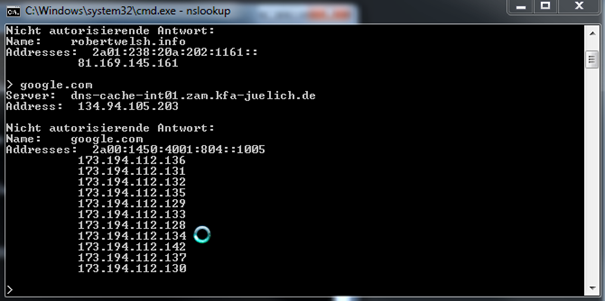
Lookup name to IP address:
DNS: Domain Name Service, one of the most important protocols on the Internet, DNS protocol translates domain names to IP address. For example cmd ping yahoo.com would resolve the domain name to the IP address 98.139.183.24
IEFT Internet Engineering Task Force
The IETF are responsible for RFC Request for comments. www.IEFT.org is the website for RFC, you can also search for network protocols, here you can find all the details about networking protocols.
More about the FTP Protocol.
In this example we logon to an FTP server using windows command prompt, this is an example of plain text method.
More about Email Protocols
In the next example we look email protocols. The picture below shows us a widely use Email client, outlook from Microsoft allows various configurations. POP3 and IMAP are one of the oldest email protocols, today email servers are smarter and make it simpler for users to configure their email accounts easier. However we will take a look at the basics of configuring an email client.
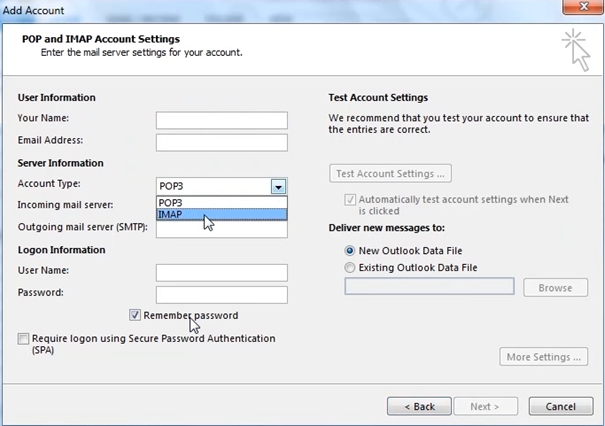
In the server Information we can select the account type, POP3 or IMAP. First POP3, the Incoming mail server box we must enter the name of the email server where we down load out mails from.
Outgoing mail server we specify the SMTP server (the server that sends your mail out).
IMAP typically used with mobile phones to send. Google mail IMAP for example can be configured on a windows Iphone or android, the email client when it uses the E-Mail server sends messagesdirectly between the phone and the email server. Generally when you configure the IMAP account you would enter the server details and the rest is configured automatic.
MS RDP protocol
This is the standard protocol for Microsoft networks, this allows a user to connect to a remote computer and view the Desktop.
Telnet and SSH
Remember Telnet sessions are not encrypted and SSH are encrypted. The both do not use a typical GUI, they both use a command prompt and look identical. The advantage of using the command prompt is that it makes ridiculously that are done with a GUI a lot simpler
Telnet and SSH via Putty
To initiate a Telnet or SSH connection we need software to do it, some systems such as Linux / Unix come with SSH / Telnet preinstalled, other Operating Systems must have an application installed to make SSH / Telnet, a common program which is used is called putty. With Putty you can pre-configure multiple sessions and save for later use. In this example I will use putty:
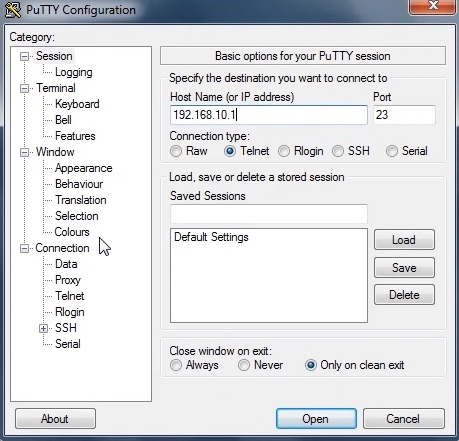
You can see in the above picture we enter the host name or IP address and select port 23 a Telnet session. Once connected you will see a terminal session open, next you will be requested to enter your username and password
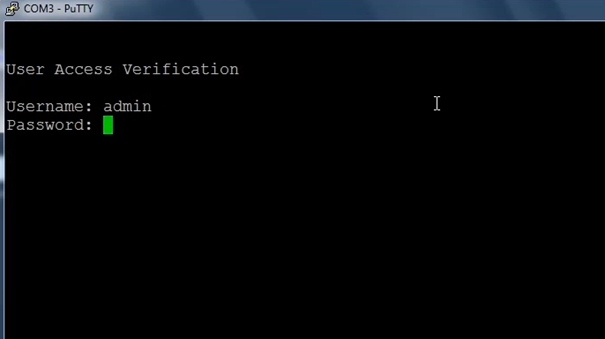
Once logged in you can enter commands that are specified to operate the device. The below picture shows an example of a user logged into a router.
Domain Name
service as said is used to resolve domain names to IP address. The advantage of
this is simply, it’s easy to remember a domain name than and IP address. The next screenshot shows NSLOOKUP command
using windows command prompt
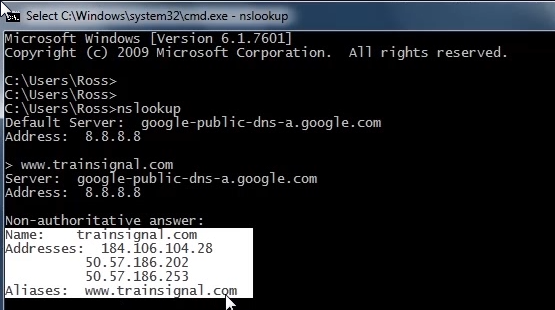
A breakdown the NSLOOKUP command
NSLOOKUP will first connect you to your DNS server; once the command is entered you can then enter a domain name, as you can see on the screenshot above you can see 3 ip addresses for trainsignal.com. The reason for 3 IP addresses, this indicates that 3 IP addresses / NICs have be allocated to the website, if one IP address is busy it could be that the NIC is overloaded, other users attempting to connect to the site would be redirected to the 2nd or 3rd NIC, this is also known as load balancing which provides availability as well as redundancy. If we try another website, for example my personal website robertwelsh.info we might see the following:
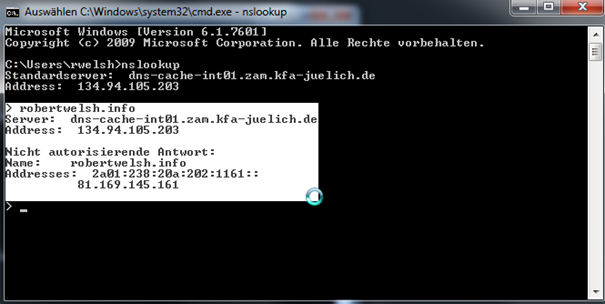
This however does not mean that there is no NIC redundancy or load balancing. Also note we can the next line above the IP address is indicating an IPV6 address, in the future this will be more widely used because IPV4 addresses have reached maximum limit on the World Wide Web.
One last example google.com, in this example you can see many IP addresses allocated